Table of Content
Your online life might feel comfortable and easy with multiple options and internet devices at your disposal.
Want to order a couch? Order it on Amazon and it will be delivered to your doorstep.
Feeling hungry? UberEats will bring fresh food in half an hour for your cravings.
But on the flip side, the big struggle to protect user data is still haunting tech companies and government agencies.
It opens doors to several hackers and scammers who will try every trick up their sleeves to steal your personal data.
How Do Hackers Collect Your Data?
Hackers use various smart strategies, frequently combining different approaches at once, to steal your data.
They use phishing, waterhole attacks, clickjacking, and fake WiFi hotspots to exploit security holes, and obtain private data that they can use or sell for additional attacks.
What Type of Information do Hackers Collect, and How?
Hackers target personal data, including passwords, addresses, birthdates, bank account information, and credit card information. With this stolen data, they can commit fraud, steal identities, or hold companies ransom.
Personal Information
- Personal Identifying Information, or PII, can be used to find, identify, or contact you. Name, birthday, SSN, and phone number are a few examples.
- Hackers frequently target PII to commit fraud, such as submitting fake tax returns or loan or credit card applications.
Financial Data
- Cybercriminals with greater expertise might even create credit cards in your name. Most fraudulent acts involving PII are applicable.
Web Access Via DoS/DDoS
- Denial of Service attacks bombard a server with erroneous requests using a botnet. The server becomes overloaded, and all of the websites hosted on it go dark.
Bait and Switch
- It is the practice of tricking consumers into clicking on enticing advertising on well-known websites. Once clicked, the ads lead to a page that downloads malware.
Password Tracking by Cookie Theft
- If a website isn't SSL-secured, a hacker may obtain cookie information—such as browsing history and passwords—and use it to verify their identity as the website's owner.
Why Is It Important to Understand the Data Privacy Laws?
Understanding privacy rules promotes confidence between people and institutions. By thoroughly understanding these rules, organizations can take measures to prevent data breaches, which can have serious consequences.
Non-compliance may harm a company's reputation and result in fines and legal action. Ethical guidelines on the proper handling of personal data are frequently reflected in privacy laws.
How to Protect Your Personal Information from Hackers
Hackers can obtain personal data and do serious damage. By following these principles, you can reduce the possibility that your personal information will end up in the wrong hands.
Here are some crucial actions you should take to stay safe:
Use a Firewall
Install a firewall to protect your data from hackers. This crucial tool warns you of suspicious activity and helps prevent unauthorized access.
Get an Antivirus Software
Installing antivirus software will protect your computer by providing real-time virus and malware detection and removal. This guarantees that your system is protected from a variety of threats.
Consider Using Antispyware
Install anti spyware software to stop programs illegally tracking and gathering your personal information. This specialized software secures against privacy breaches caused by spyware.
Secure Your Network with Strong Password
Set up a password and strong encryption on your router to prevent unwanted access to your network. Secure networks prevent hackers from accessing your computer.
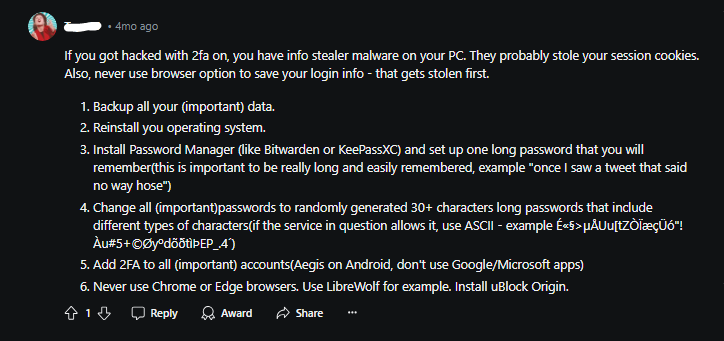
Turn on Two-Factor Authentication
Enable two-factor authentication to add a degree of protection. This protects your accounts by requiring a verification code and your password.
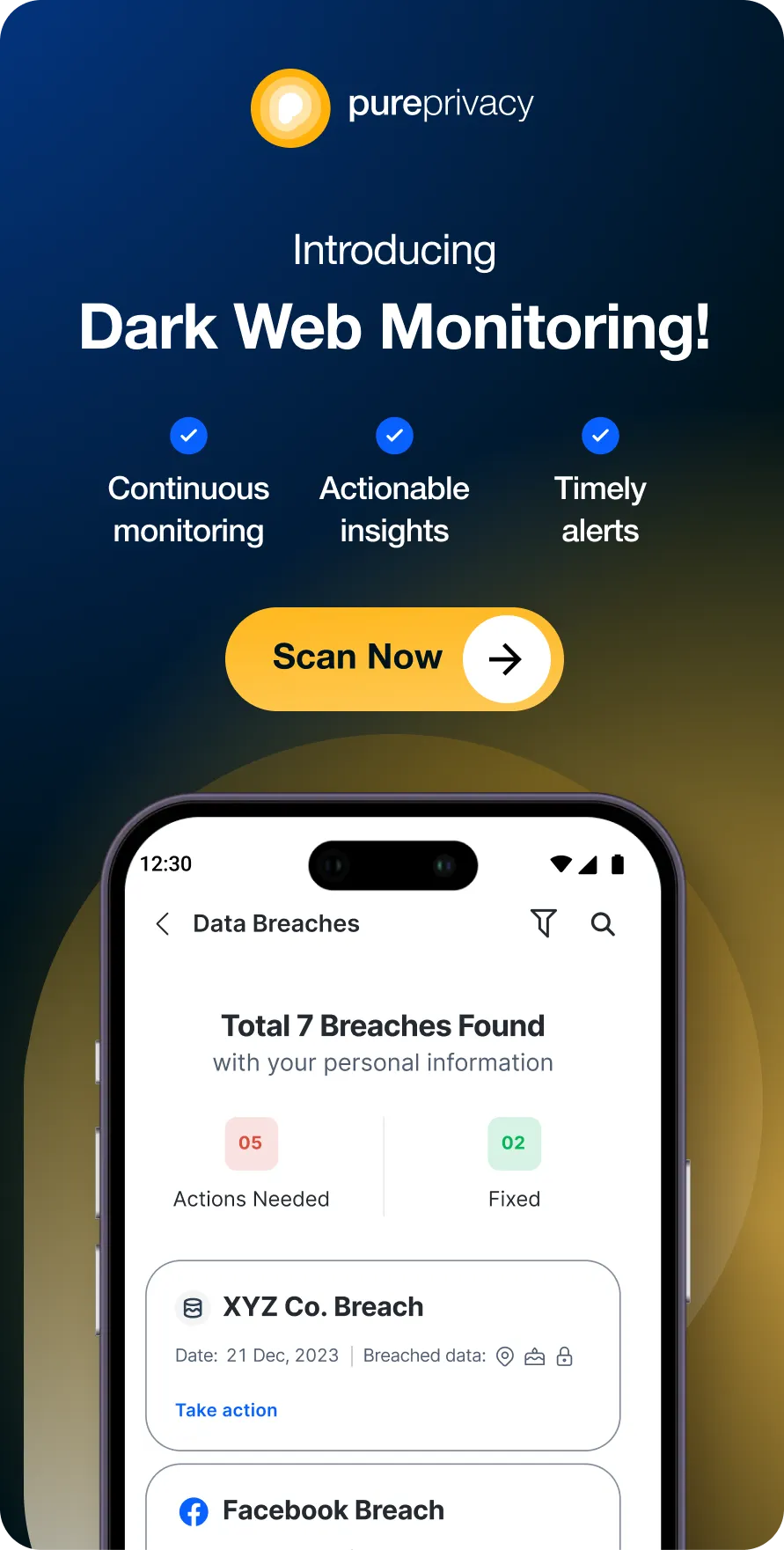
- Use Dark Web Monitoring to scan the dark web for your data and get alert notifications if someone posts your data on the dark web.
- Use Tracker Blocker to stop websites and unwanted trackers from online tracking and data collection.
- Use Remove My Data to send information removal requests to data broker sites.
- Use Social Privacy Manager to use social media without worrying about tracking or analyzing your online activities.
Monitor the Dark Web 24/7
PurePrivacy searches the dark web for your personal data, assisting you in addressing security risks before they affect you and guaranteeing the security of your identity.
Block Invisible Trackers
Use the Tracker Blocker to prevent unwanted tracking and lowers the possibility of targeted advertisements and data misuse.
Send Data Removal Requests
By automatically requesting the removal of their personal data from data brokers, you can take proactive steps to boost your privacy.
Auto Delete Search History
You can delete your search history from several social media sites and can drastically reduce the amount of personal information that is publicly available online.
Frequently Asked Questions (FAQs)
-
How can I ensure my online privacy?

To maintain your privacy, use strong, one-of-a-kind passwords for all your accounts and turn on two-factor authentication. Also, use antivirus and antispyware software, update your software frequently, and exercise caution when disclosing personal information online.
-
How effectively can I strategize my data usage?

Adopting strong security measures, like data encryption, frequent backups, and restricting access to sensitive data, are all necessary for efficient data usage strategies. Routine audits and risk assessments make maintaining current and successful data protection strategies easier.
-
How do hackers use my personal information?

Cybercriminals can easily use privileged intellectual property (PII). They might file fictitious tax returns in your name and apply for credit cards or loans. Or they could send you spam for the rest of your life.
-
How do cyberattackers protect themselves?

Two-factor authentication is a common technique for preventing hackers from accessing personal data. However, using actual contact details is extremely dangerous for hackers. To protect their privacy, hackers employ burner phones, several fictitious email addresses, and fully encrypted communications systems like Signal.
In Conclusion!
Even if you are not a target victim of any data breach yet, there are some security measures that should be normalized in the ever-growing era of data breaches.
You have to be wary of online threats, including checking your credit score before buying a car, be careful of phishing scams, and learn how to protect personal data before it falls in the wrong hands.
It's critical to keep sensitive information safe from hackers.
You can use PurePrivacy with a VPN to block multiple internet trackers, use dark web monitoring, enhance social media privacy, and remove your data automatically.