Table of Content
- How Can I Check If My Credit Card Is Posted on the Dark Web?
- What Should I Do to Protect My Credit Card Information from Dark Web Leaks?
- How Did My Credit Card Information Appear on the Dark Web?
- Is It Possible to Remove My Credit Card Information from the Dark Web?
- Protect Your Data from Cybercriminals With PurePrivacy
- Frequently Asked Questions (FAQs)
- In Conclusion!
Since the early 2000’s, the dark web has transformed into a big, gigantic marketplace for illicit activities and trade.
Activities like selling stolen credit card details and accounts thrive in these dark corners of the internet.
Can you imagine losing your life’s savings because of a small data breach?
Even the idea of data theft can be traumatizing for many individuals like us.
But we can’t deny the facts!
As of 2023, the dark web had about 2.5 million daily visitors, and over 1.2 million payment card details were leaked on the Dark Web by 2022.
How long can you protect your data from these cunning hackers?
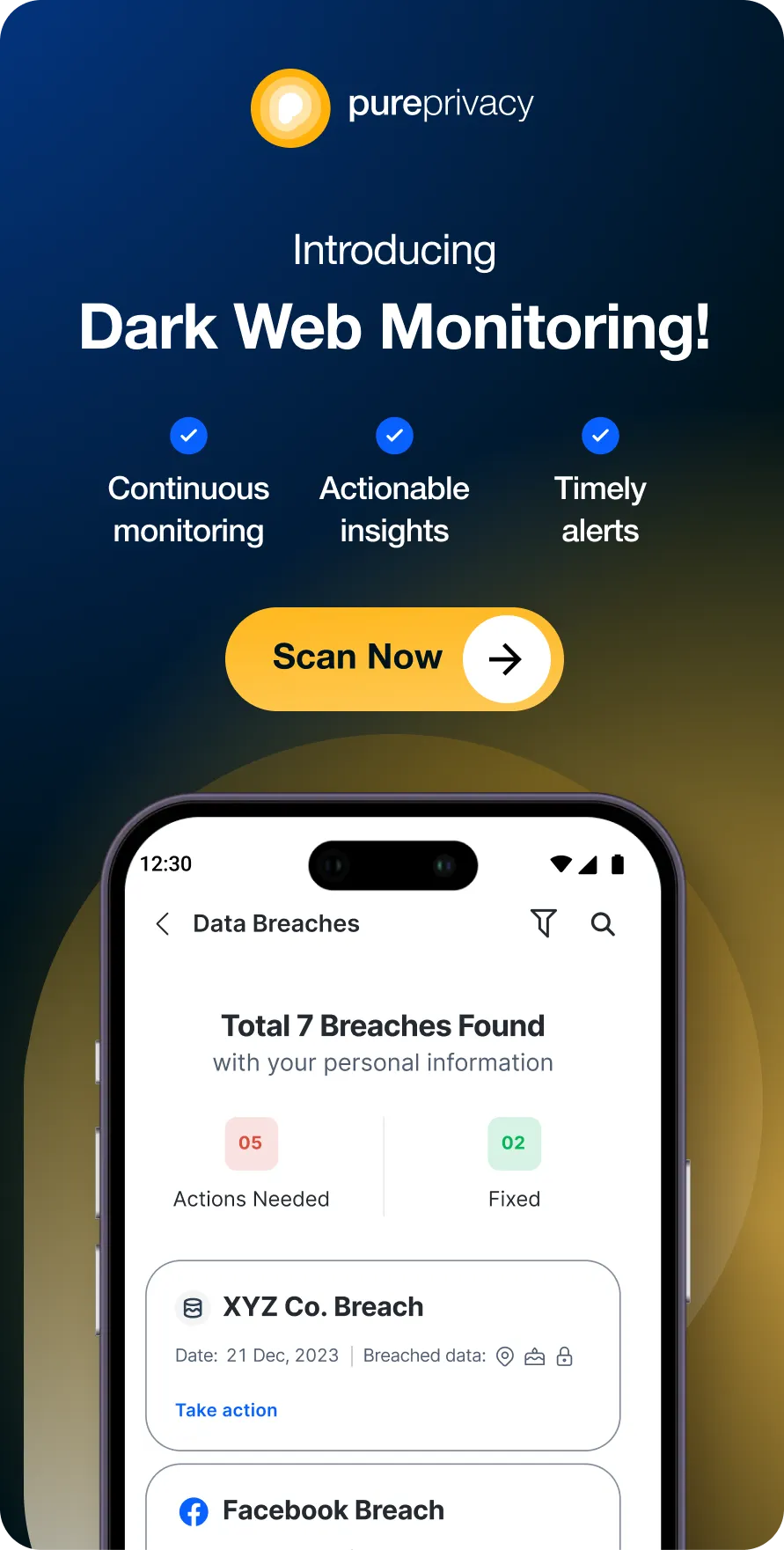
Discover if Your Most Critical Identifiers Have Been Exposed on the Dark Web
Receive timely alerts and actionable insights with PurePrivacy's Dark Web Monitoring.
How Can I Check If My Credit Card Is Posted on the Dark Web?
You cannot instantly verify whether your credit card details are available on the dark web or not.
The dark web is a secret internet section that cannot be found using conventional search engines like Google or Bing.
You need a specialized Tor browser to use the dark web.
It's not easy to look for specific information because it's designed to maintain user anonymity.
Some services claim to search the dark web for stolen data, but their efficiency is questionable!
It's critical to realize that these services do not provide 100% coverage.
The most effective strategy is to monitor your credit reports closely, register for fraud alerts from your bank, and exercise caution when using the Internet.
Credit card fraud goes down like this, the cards are stolen, they are then linked to Paypal, from Paypal they can transfer any amount from the bank account and then withdraw to MPESA.
— Post Carlone (@carltonkitheka1) January 8, 2024
This is what kina Frank Obegi were doing and that's what got them killed. https://t.co/Nv0Mm2vWP6
What Should I Do to Protect My Credit Card Information from Dark Web Leaks?
You should take immediate action if you believe you are the victim of a data breach, such as if your credit card has been used for several fraudulent transactions.
You can take the following actions if your information is discovered on the dark web.
Use Anti-Malware App
To stop malware in its tracks, update your antivirus software and do routine scans.
Set Complex, Unique Passwords
Strengthen your passwords and make them distinct for each account.
Consider using a password manager and enable multi-factor authentication for significant accounts.
Check Your Credit Report Frequently
Continually check your credit record for any unusual behavior.
Report identity theft to the credit bureaus and let them know if you see anything unusual.
Freeze Your Credit Cards If Need Be
Consider freezing your credit to increase security and prevent fraudulent accounts from starting in your name.
Be Wary of Phishing Scams
Be watchful for strange links and refrain from responding to emails from senders you don't recognize.
Stay vigilant while sharing information online, particularly on social media platforms where hackers are on the lookout for vulnerable victims.
How Did My Credit Card Information Appear on the Dark Web?
Sensitive information can be stolen in many ways, such as public data breaches and hacked online accounts. Recognizing these risks and taking precautions to protect your financial stability and privacy.
Data Breaches
A corporation may have a breach that exposes personally identifiable information (PII) about its customers or employees.
Cybercriminals gather data that has been compromised and post it on the dark web.
Affected Online Bank Accounts
Compromised online accounts may result in credit card details ending on the dark web.
Accounts can become vulnerable to penetration due to weak password habits, such as using the same password for many accounts.
Credit Card Skimming
Threat actors use devices called credit card skimmers to obtain credit card information.
The threat actor receives the card information when the victim swipes or inserts their card through Bluetooth.
Using Unsafe WiFi Network
Man-in-the-middle (MITM) attacks can compromise sensitive data using an unprotected WiFi network.
Cybercriminals can intercept data transmitted between two persons on public WiFi networks.
Clicking Spoofed Website Links
Personal data may be stolen when credit card details are entered on spoof websites.
Although spoof websites appear authentic, their true purpose is to steal your personal data.
Is It Possible to Remove My Credit Card Information from the Dark Web?
No, it is difficult or impossible to remove your information from the dark web once it has been posted.
Dark web archives of stolen personal information typically serve to further illicit activities.
If an administrator could be reached, they probably wouldn't respond to your message.
Even if you can remove your information from one dark web address, you cannot guarantee that it hasn't been duplicated or placed on other websites.
Change your passwords, contact your credit card companies, and do not delete the compromised information to ensure that the stolen data becomes irrelevant.
The Hidden Wiki
— Tulsi Soni (@shedntcare_) August 12, 2024
It serves as a community-edited .onion Wikipedia, offering a plethora of Tor links to various dark web services and sources.
However, many links may be inactive or lead to illicit activities, so caution is advised when exploring. pic.twitter.com/0NT4mTV3yA
Protect Your Data from Cybercriminals With PurePrivacy
PurePrivacy offers privacy-focused features allowing you to browse the internet with confidence and complete privacy.
- Use Dark Web Monitoring to get real-time alerts for compromised personal information on the dark web. This will help you stay one step ahead of data thieves.
- Use Tracker Blocker to prevent intrusive tracking and advertising cookies. This will allow you to enjoy an ad-free and more customized surfing experience.
- Use Remove My Data to remove your information data broker databases and lower your risk of unsolicited marketing and spam.
- Use Social Privacy Manager to manage your social media privacy settings with a single click.
Prevent Identity Fraud With Dark Web Monitoring
Detect and remove unwanted access to your personal data on the dark web to prevent identity theft.
Stop Unwanted Access and Online Tracking
Reduce intrusive tracking cookies that slow down your browsing experience while compromising your online privacy.
Remove Your Data With Opt-Out Requests
You can follow the progress of your information removal requests and stop unnecessary data collection.
Boosts Your Social Media Privacy Settings
Maintain your online privacy by restricting the amount of personal information social media sites can collect and use.
Frequently Asked Questions (FAQs)
-
How can I keep credit card scanners away from me?

Invest in an RFID wallet or card sleeve that prevents RFID transmissions.
Stack your cards together to reduce the amount of information the scanner can read.
You should only use cash in public areas and leave your cards at home. -
What happens if my SSN appears on the dark web?

As soon as you discover that your SSN is accessible on the dark web, take measures to lessen the impact on you. Place a fraud alert on your credit report by contacting the FTC and following the six steps mentioned above. Contact the FTC at www.ftc.gov/idtheft or 1-877-438-4338.
-
Is it possible to find out who used my credit card online?

No. On the other hand, if you report the fraud promptly, the bank or card issuer will launch an inquiry. Banks have protocols for investigating credit card fraud, including several common practices.
-
How do hackers continue to obtain my credit card information?

Hackers can access credit card numbers and other information stored on your computer if you unintentionally download malware or spyware. A keylogger, for instance, might be used in a malware assault to capture your keystrokes or browser history and then transmit that data to a hacker.
In Conclusion!
When technology is neither impactful nor proactive, it becomes obsolete faster.
To stay protected in such testing times, you need quick insights into the dark web and reliable sources to monitor online threats.
Identity theft and other online scams are becoming more common than you imagine.
And to prevent your personal information from falling into the wrong hands, consider using PurePrivacy with a VPN.