Table of Content
- What Happened in the Fortinet Data Breach?
- What Was the Impact on Fortinet Customers?
- What was Fortinetâs Response on this Data Breach?
- What are the Potential Privacy Risks from Exposed Data?
- How to Take Immediate Action in Case of a Data Breach
- Protect Yourself from Identity Theft & Doxxing With PurePrivacy
- Frequently Asked Questions (FAQs)
- In Summary!
How ironic!
One of the top cybersecurity companies, Fortinet, experienced a data breach that exposed 440GB of private information.
A threat actor got access to multiple cloud files via a shared drive, but he didn’t breach the main corporate network.
Fortinet is a big cybersecurity vendor providing detection, VPN, and firewalls.
But the online privacy of even the most advanced cyber security firm is seriously called into doubt in light of this extraordinary attack.
Let’s find out what type of data was made public and the potential effects it can have on your online identity.
What Happened in the Fortinet Data Breach?
The Microsoft Azure SharePoint server of the massive cybersecurity company Fortinet was significantly compromised in September 2024.
A threat actor claims to have stolen 440 GB of data, including client information, corporate papers, and possibly sensitive financial data.
The threat actor is thought to be associated with an organization with connections to Russia.
The specific reason for the hack is still being looked into, although it's possible that the attackers took use of security holes in the SharePoint server or other Fortinet networked systems.
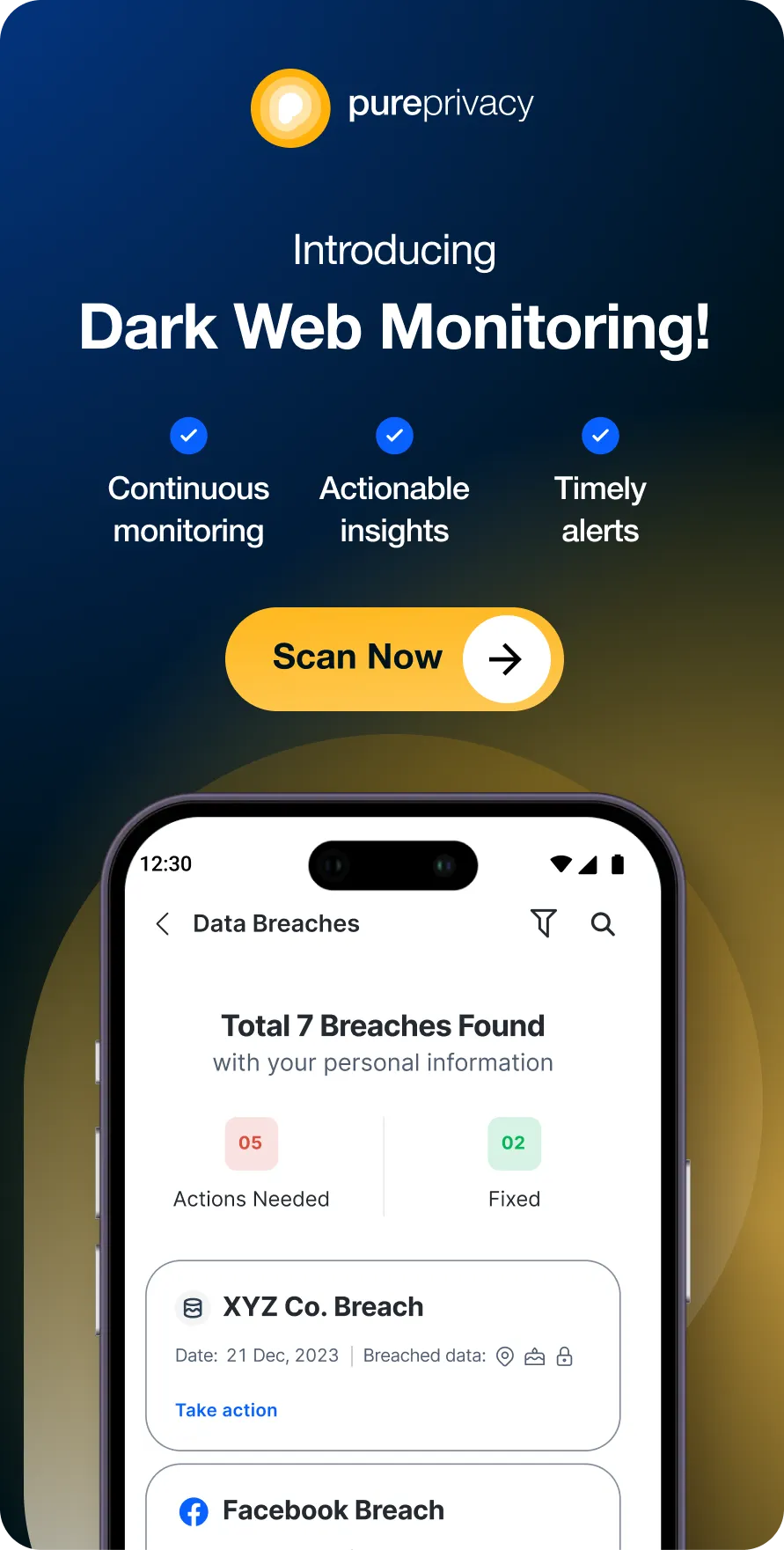
Discover if Your Most Critical Identifiers Have Been Exposed on the Dark Web
Receive timely alerts and actionable insights with PurePrivacy's Dark Web Monitoring.
What Was the Impact on Fortinet Customers?
The threat actor, identified as "Fortibitch," revealed login details to an S3 bucket, an online file storage platform, containing 440GB of downloadable content.
Fortinet confirmed today that it suffered a breach of its cloud storage environment that impacted customer data.https://t.co/KlaH71IBjN
— CRN (@CRN) September 12, 2024
Fortinet rejected the requests in the face of an extortion attempt. Although the company has not disclosed the precise data that was stolen, it has already informed the impacted users.
The hacker brought up Fortinet's recent acquisitions, which included cloud security startup Lacework and Data Loss Prevention (DLP) business Next DLP.
The hacker went on to say that Fortinet's Azure SharePoint was infiltrated, which made it possible to get the sizable data cache.

He claimed that he attempted to blackmail Fortinet into paying a ransom—possibly to stop data from being published—but the company denied it.
The CEO of Fortinet replied hacker:
"he would rather eat some p**p then pay the ransom."
What was Fortinet’s Response on this Data Breach?
Fortinet clarified the amount of compromised data in a statement.
They claim:
“An individual gained unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party cloud-based shared file drive, which included limited data related to a small number of Fortinet customers.”
Fortinet has underlined how dedicated it is to protecting clients and upholding the credibility of its business operations. Less than 0.3% of the company's clientele was impacted, the company confirmed.
To be clear, Fortinet stated that there is currently no proof that any customers have been harmed by malicious activity as a result of this issue.
What are the Potential Privacy Risks from Exposed Data?
To protect your personal information and keep an eye out for any suspicious activity, it is recommended that you closely monitor your accounts to avoid these cyber security risks:
Identity Theft
Exposure of personal information can lead to identity theft, fraudulent account opening, and other financial offenses.
Cyber Extortion
Cyberthreat actors can blackmail people, companies, or even countries using the stolen data.
Phishing Tactics
Hackers can use stolen information to craft more convincing phishing emails.
Social Engineering Attacks
Information that has been compromised can be used to blackmail people into disclosing private information or acting in ways that would help the attacker.
Pretexting is a social engineering tactic where an attacker creates a fabricated scenario or identity (a "pretext") to manipulate a target into revealing sensitive information. The attacker often pretends to be someone trustworthy to gain access to passwords and personal data. pic.twitter.com/FeWmEiNY0h
— Claire ✨ (@ociyara) September 6, 2024
How to Take Immediate Action in Case of a Data Breach
You can protect yourself and your company from the consequences of a data breach by taking the actions outlined here and, if needed, consulting a cybersecurity expert.
Comply with the Data Security Laws
Data breaches must be reported by organizations to the appropriate authorities within 72 hours of inquiry.
If there is a significant risk, individuals impacted by breaches must also be informed. Similar reporting requirements apply to regulations such as DORA and GDPR.
Enable Encryption Protocols
Use end-to-end encryption while handling sensitive data. This implies that even if the data is compromised, it won't be "readable."
Set Multiple-Factor Authentication
Make sure MFA is in place to secure sensitive data and important systems. This might consist of a password and a one-time passcode that is texted to a reliable mobile device.

Use Intrusion Detection Systems
IDS may monitor network traffic and alert you to both routine and unusual activity.
Get Personalized Data Security Software
Implement customized software to stop data breaches in the future. These solutions, which are customized to your organization's particular requirements, provide improved security and protection for critical data.
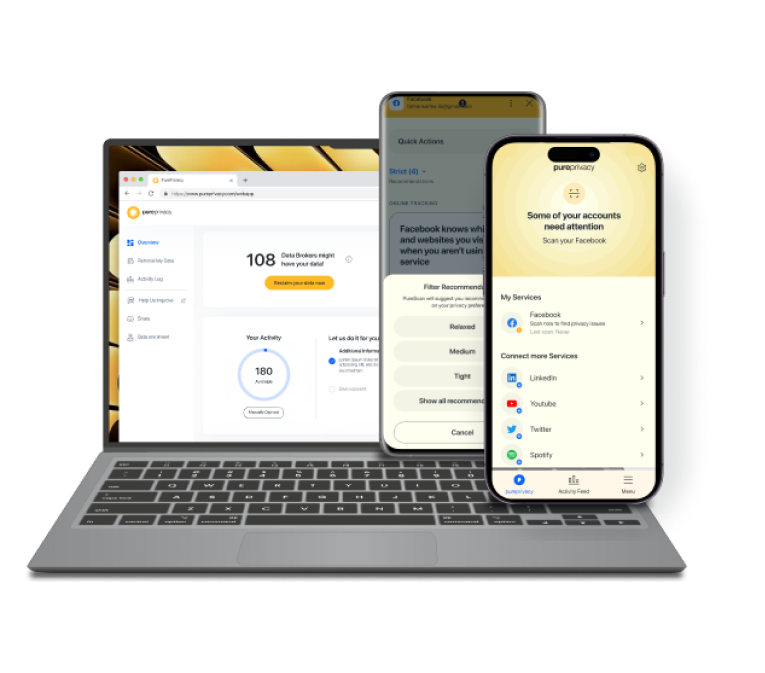
Protect Yourself from Identity Theft & Doxxing With PurePrivacy
Having a strong online security solution is essential due to the ongoing threat of identity theft and cyberbullying.
PurePrivacy provides you with a risk-free online experience by keeping you away from hackers and data brokers.
- Dark Web Monitoring: Search the dark web for personal data leaks, including credit card numbers, social security numbers, and passwords.
- Tracker Blocker: Stop websites and outside trackers from gathering and using your browsing information.
- Remove My Data: Reduce the risk of identity theft by keeping your private information less accessible to possible attackers.
- Social Privacy Manager: Manage the privacy settings on well-known social media sites to protect your private data from unwanted access.
Scan the Dark Web for Data Leaks
Get notified immediately if any of your data is discovered, giving you time to take appropriate action and stop additional harm.
Block Internet Trackers from Data Collection
Get a more customized online experience by protecting your privacy and assisting in reducing targeted advertising with tracker blocker.
Send Automated Opt-Out Requests to Data Brokers
Remove your personal data automatically from websites run by data brokers, which frequently sell your data to outside parties.
Manage Social Privacy Settings
By auto-deleting your search history from social media, you can improve your privacy. Lower the possibility that your personal information will be misused by deleting your search history. ssess and refine your social media privacy settings for enhanced security across multiple platforms.
Frequently Asked Questions (FAQs)
-
In what ways can I lower the risk of a data breach?

Certain steps in the plan that reduce the chance of a data breach include secure data handling in remote work policies, strong password regulations, and routine software updates.
-
How can data breaches be identified?

The most effective way to do this is with an attack surface monitoring tool. This kind of solution will identify any security flaw in your ecosystem as well as in your network of third-party vendors.
-
How do companies manage data leaks?

They mostly use anti-virus, anti-spyware, and firewall software to protect their company from data breaches. To properly set things up, they collaborate closely with an internet security team or supplier.
-
Can data breaches be avoided with encryption?

The best encryption solutions save data in an encrypted manner. When sensitive data is encrypted, hackers are unable to access it.
In Summary!
The Fortinet’s hacker statement, “I’m not selling it. It’s completely free and already published. I will share the data another way,” underscores the stark reality of massive data breaches.
And such attacks, often motivated by fun and amusement, highlight the dire need for cybersecurity measures.
When it comes to online privacy, PurePrivacy with a VPN provides a rock-solid solution to keep your data private and inaccessible.