Table of Content
Has someone accessed your private information, and you don't know it?
The cyber world continues to shake from the Zeeroq data breach, leaving millions exposed to the prying eyes of cybercriminals.
This unfortunate incident has publicized much private information, prompting concerns about internet security and privacy.
What Happened in the Zeeroq Data Breach?
Zeeroq.com, a well-known online portal, has experienced a significant security compromise. When the breach was discovered in January 2023, private user data, including emails and passwords, was revealed.
Cybersecurity firms searched the dark web for security flaws and found the breach.
The scan showed that Chucky, a hacker, had taken user data from Zeeroq and posted it on leakbase.io. 8.71 GB of data was stolen and disseminated, according to startling information.
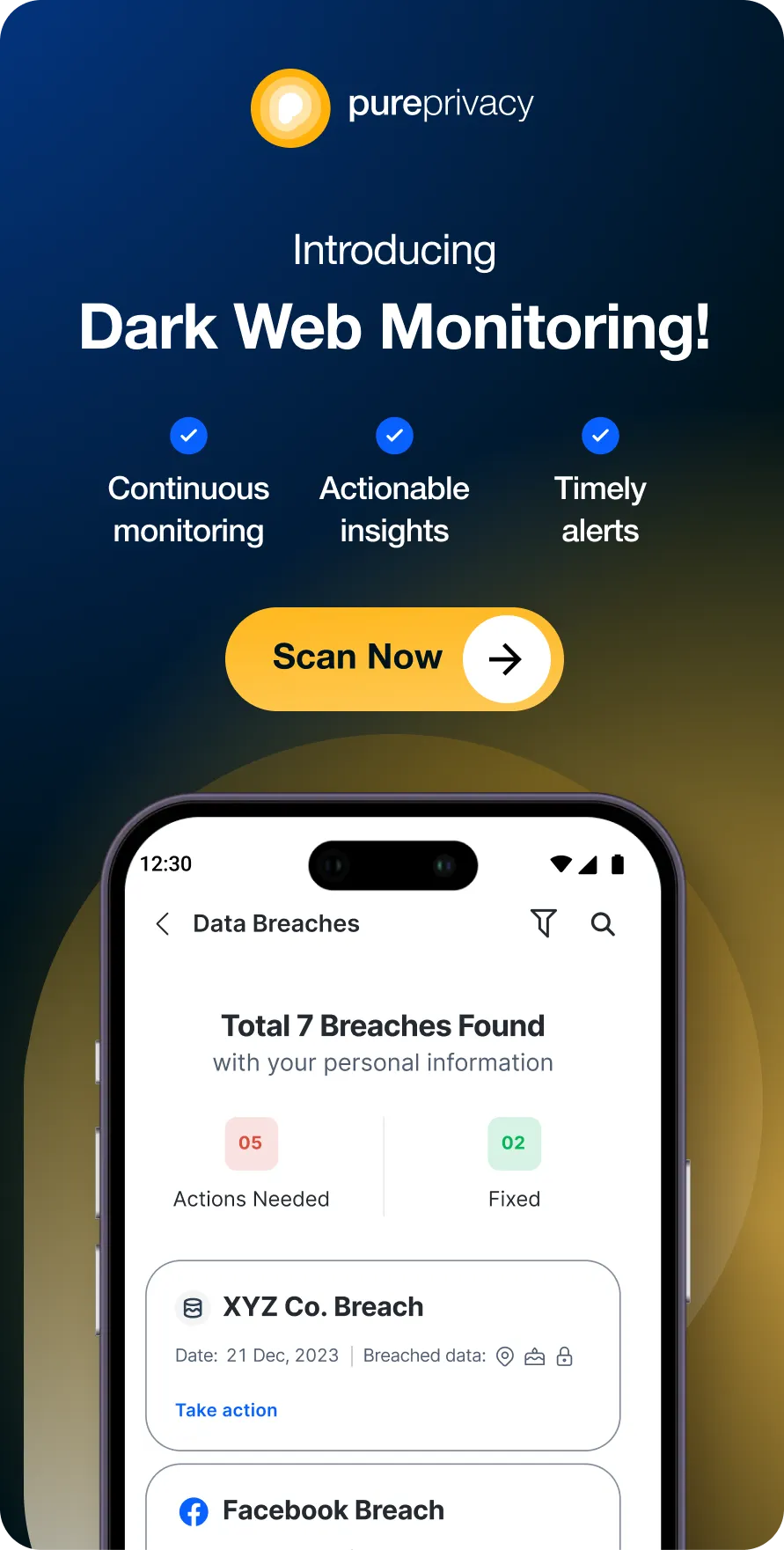
Discover if Your Most Critical Identifiers Have Been Exposed on the Dark Web
Receive timely alerts and actionable insights with PurePrivacy's Dark Web Monitoring.
Before this occurrence, there was no known history of security breaches on Zeeroq.com.
According to recent reports of January 2024, the compromised data originated from multiple sources in addition to one particular company. The exposed information came from several sources totaling 26 billion, making it a unique breach known as the Mother of All Breaches (MOAB).
However, it is challenging to determine whether the data breach affected Zeeroq alone or other websites. Aside from what we already know—passwords and emails—no one can say what information was disclosed.
What was the Impact on Zeeroq Customers?
Word of the data leak quickly spread throughout the online community, shocking users globally. And, panic broke out when the first news surfaced that the compromised data contained emails, passwords, and private images.
Most of us feared malicious hackers would use our photos to produce false information or run deepfake attacks.
The data may be used in phishing emails, scam networks, or movies. This could significantly impact your personality, career, and financial situation, particularly if you're an entrepreneur.
Zeeroq Data Breach Exposes Millions of Users
Zeeroq.com's hack happened on a renowned Dark Web forum notorious for encouraging illicit activity. Chucky, the hacker in question, got the database from zeeroq.com on this hidden marketplace.
Passwords and emails were among the compromised data, which was later exposed to possible cybercriminals.
The compromised information is dangerous to the impacted users, given its potential for several evil uses such as fraudulent identity theft, deceptive email schemes, and unapproved entry into other virtual accounts.
Recognizing the potential impact on its consumers, Zeeroq.com quickly protected user data. The first action was to release a statement promising their clients that every effort was being made to stop the situation.
The organization demonstrated even more dedication when they said they were collaborating with cybersecurity specialists to understand the issue and secure it fully. Users also received free credits to have their accounts watched over to prevent more hacking.
What are the Potential Privacy Risks from Exposed Data?
For anyone impacted, the disclosure of Zeeroq data poses serious privacy implications. Here are the following associated privacy risks:
Fabricating Personal Information
It is possible to fabricate an identity using publicly available information, such as names, addresses, and social security numbers.
Stealing Financial Information
Unauthorized transactions and financial loss can result from using credit card numbers, bank account information, and payment histories.
Phishing Attacks
To increase their chances of success, hackers might generate highly tailored phishing emails using publicly available data.
Social Engineering
By establishing trust and persuading victims to disclose private information, stolen information can be used.
Blackmailing and Extortion
Victims may be subjected to blackmail or extortion by the exploitation of exposed personal information.
Doxxing
Hackers and scammers can harass or intimidate you using private data (photos, messages, secrets), or even run impersonation attacks.
How to Take Immediate Action in Case of a Data Breach
You should take the following precautions to protect yourself against account compromise and personal information theft:
- Regularly update their passwords using a mix of characters, digits, and symbols.
- Whenever feasible, turn on two-factor authentication.
- Ensure every account has a different password to avoid hackers using the same password to access several accounts.
- Examine your credit record for any suspicious requests or accounts.
- Be wary of dubious emails or texts since they can include phishing links that could jeopardize their accounts.
- Look closely at their accounts to look for any unusual behavior.
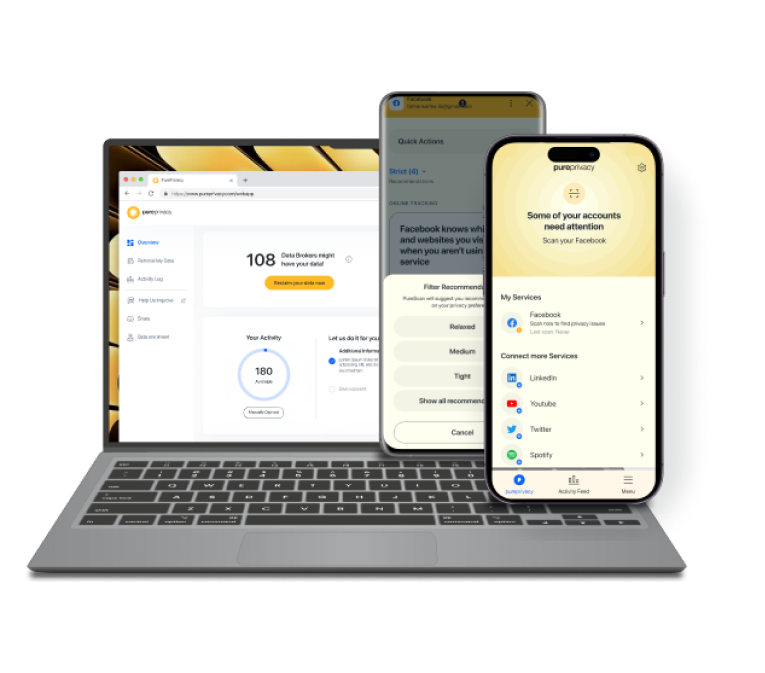
Monitor the Dark Web 24/7
You can use PurePrivacy to search the dark web for publicly available personal data and get alert notifications if someone posts your information without consent.
View & Send Information Removal Requests
Allows you to request the removal of your data from public websites and data brokers, thereby assisting you in exercising your right to privacy.
Get a Tailored Privacy Scan
You can assess and look for privacy flaws on your social media accounts and receive practical solutions on how to upgrade online privacy.
Reduce Targeted Ads & Tracking
A tracker blocker protects you against behavioral profiling and targeted advertising by stopping websites and third-party trackers from gathering your personal information.
Frequently Asked Questions (FAQs)
-
What is the reason behind the notification I received regarding a data leak?

Remain calm if you receive a notification on your phone indicating a data leak. Yes, it suggests that there has been a data breach involving your data, allowing unauthorized users to access your accounts and personal data.
-
What happens in the event of a data breach?

Data made public during a hack creates a major fraud risk. Following a data breach, the following sensitive data could end up in the hands of criminals or on the dark web: your entire name and email address.
-
What is the process for identifying a data breach?

The process of detecting and reacting to unauthorized access to data within an organization is known as breach detection. It involves looking for signs of data breaches, such as strange network behavior, efforts to access data without authorization, and unforeseen database modifications.
In Conclusion!
The Zeeroq data incident highlights the vital need for strong cybersecurity measures.
These incidents draw attention to weaknesses in even well-established systems and their possible negative effects on consumers.
Consider using PurePrivacy to carefully monitor the dark web for your private data, block multiple internet trackers, send recurring data removal requests, and enhance social media privacy settings.